Certified Security Defense Engineer (CSDE) Industry-Standard Cybersecurity Defense Certification
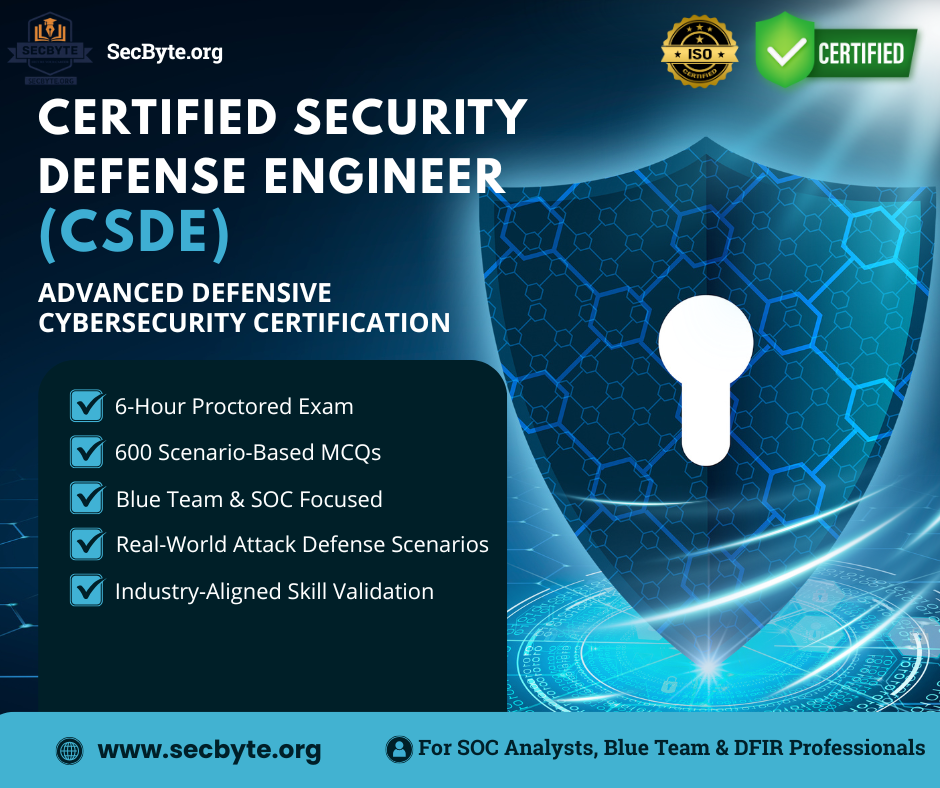
The Certified Security Defense Engineer (CSDE) is an advanced, industry-aligned cybersecurity certification designed to validate real-world defensive security skills across modern enterprise environments. This certification is built for professionals who are responsible for detecting, analyzing, and responding to cyber threats rather than merely understanding theoretical concepts.
CSDE focuses on practical defense scenarios that reflect the challenges faced by today’s Security Operations Centers (SOC), blue team professionals, and incident response teams. The exam assesses a candidate’s ability to interpret security events, respond to active threats, and apply defensive controls under realistic constraints.
Unlike traditional certifications that rely on memorization, CSDE uses scenario-based multiple-choice questions that simulate real incidents such as malware outbreaks, insider threats, network intrusions, cloud misconfigurations, and data exfiltration attempts. Candidates must analyze logs, alerts, architectures, and response options to determine the most effective defensive action.
The CSDE examination is a 6-hour, 600-question assessment, making it one of the most comprehensive evaluations of defensive cybersecurity knowledge available. It is designed to test endurance, analytical thinking, and decision-making accuracy under pressure — essential traits for security defense engineers.
This certification is vendor-neutral and aligned with industry best practices, frameworks, and real operational workflows. CSDE is suitable for professionals seeking to demonstrate advanced competency in network defense, threat detection, incident response, vulnerability management, and security monitoring.
By earning the CSDE credential, candidates prove their readiness to defend modern digital infrastructure against evolving cyber threats and establish themselves as trusted security defense professionals.
Exam Overview
-
Exam Duration: 6 Hours
-
Total Questions: 600
-
Format: Multiple-Choice (Scenario-Based)
-
Delivery: Individual Online Examination
-
Certification Type: Vendor-Neutral
-
Focus Area: Defensive Cybersecurity (Blue Team)
Who Should Take CSDE
-
SOC Analysts (Tier 1–3)
-
Blue Team Engineers
-
Incident Response & DFIR Professionals
-
Security Operations Engineers
-
Cybersecurity Analysts
-
Defensive Security Practitioners
Certified Security Defense Engineer (CSDE)
Official Exam Syllabus
Domain 1: Cybersecurity Defense Fundamentals
-
Defensive security principles and blue team mindset
-
Security control types: preventive, detective, corrective
-
Threat landscape and attacker motivations
-
Security governance and defense strategy
-
Risk-based security decision making
Domain 2: Enterprise Network Architecture & Defense
-
Enterprise network models and segmentation
-
Defense-in-depth architecture
-
Secure network design principles
-
Trust boundaries and data flow analysis
-
Network hardening strategies
Domain 3: Network Protocols & Traffic Analysis
-
TCP/IP stack and protocol behavior
-
DNS, HTTP/S, SMTP, FTP, SMB abuse
-
Network traffic baselining
-
Identifying anomalous and malicious traffic
-
Encrypted traffic visibility challenges
Domain 4: Network Security Controls
-
Firewalls (stateful, NGFW, WAF)
-
IDS/IPS deployment and tuning
-
Network access control (NAC)
-
Zero Trust network concepts
-
Secure remote access (VPNs, ZTNA)
Domain 5: Endpoint Security & EDR
-
Endpoint attack surface analysis
-
EDR/XDR architecture and telemetry
-
Endpoint hardening techniques
-
Persistence detection on endpoints
-
Behavioral vs signature-based detection
Domain 6: Malware Defense & Analysis
-
Malware types and delivery mechanisms
-
Malware execution and persistence techniques
-
Fileless and living-off-the-land attacks
-
Malware detection strategies
-
Defensive response to malware incidents
Domain 7: Vulnerability Management
-
Vulnerability discovery and scanning
-
Risk scoring and prioritization
-
Patch management strategies
-
Misconfiguration risks
-
Vulnerability exploitation indicators
Domain 8: Threat Intelligence & Adversary Analysis
-
Threat intelligence lifecycle
-
Indicators of Compromise (IOCs)
-
Tactics, Techniques, and Procedures (TTPs)
-
Intelligence-driven defense
-
Threat actor profiling
Domain 9: Logging, Monitoring & Telemetry
-
Log sources across enterprise environments
-
Log normalization and enrichment
-
Centralized logging architecture
-
Telemetry correlation techniques
-
Log retention and compliance considerations
Domain 10: SIEM & Detection Engineering
-
SIEM architecture and data pipelines
-
Detection logic and correlation rules
-
Alert fatigue reduction
-
Use-case development
-
Detection testing and validation
Domain 11: Security Operations Center (SOC) Operations
-
SOC structure and responsibilities
-
Alert triage and prioritization
-
Escalation workflows
-
Incident documentation
-
Metrics and performance measurement
Domain 12: Incident Detection & Analysis
-
Incident identification methods
-
False positives vs true positives
-
Event correlation and timeline creation
-
Root cause analysis
-
Incident severity classification
Domain 13: Incident Response & Handling
-
Incident response lifecycle
-
Containment and eradication strategies
-
Business impact analysis
-
Recovery planning
-
Post-incident reporting
Domain 14: Digital Forensics Fundamentals
-
Forensic principles and evidence handling
-
Disk and memory artifacts
-
Log-based investigations
-
Chain of custody
-
Forensic readiness
Domain 15: Identity & Access Management (IAM)
-
Authentication vs authorization
-
Privilege escalation detection
-
Identity-based attacks
-
Access control models
-
Identity monitoring and defense
Domain 16: Cloud Security Defense
-
Cloud shared responsibility model
-
Cloud logging and monitoring
-
Cloud attack detection
-
Misconfiguration risks
-
Cloud incident response
Domain 17: Web & Application Security Defense
-
Common web attacks (OWASP Top 10)
-
Application logging and monitoring
-
WAF deployment and tuning
-
Secure API defense
-
Application-layer incident response
Domain 18: Email & Messaging Security
-
Phishing and social engineering defense
-
Email authentication mechanisms
-
Malware delivery via email
-
User-reported incident workflows
-
Email threat response
Domain 19: Data Security & Protection
-
Data classification and handling
-
Data loss prevention (DLP)
-
Encryption at rest and in transit
-
Insider threat indicators
-
Data breach response
Domain 20: Insider Threat Detection
-
Insider threat types
-
Behavioral monitoring
-
Privilege misuse detection
-
Investigation techniques
-
Insider incident response
Domain 21: Security Automation & SOAR
-
Automation concepts in SOC
-
Playbooks and workflows
-
Alert enrichment automation
-
Response orchestration
-
Automation risk management
Domain 22: Threat Hunting
-
Threat hunting methodologies
-
Hypothesis-driven hunting
-
Data sources for hunting
-
Hunting metrics
-
Translating hunts into detections
Domain 23: Advanced Persistent Threat (APT) Defense
-
APT characteristics
-
Long-term intrusion detection
-
Lateral movement indicators
-
Persistence and evasion techniques
-
APT response strategies
Domain 24: Ransomware Defense & Response
-
Ransomware attack lifecycle
-
Detection and containment
-
Backup strategy validation
-
Business continuity considerations
-
Recovery decision-making
Domain 25: Operational Technology (OT) & IoT Security
-
OT/ICS security fundamentals
-
IoT threat landscape
-
Monitoring non-traditional assets
-
OT incident response challenges
-
Safety vs security considerations
Domain 26: Compliance, Risk & Security Frameworks
-
Security standards and frameworks
-
Risk assessment methodologies
-
Audit preparation
-
Policy enforcement
-
Control effectiveness monitoring
Domain 27: Security Metrics & Reporting
-
SOC metrics and KPIs
-
Executive reporting
-
Incident trends analysis
-
Measuring detection effectiveness
-
Continuous improvement
Domain 28: Business Continuity & Disaster Recovery
-
BC/DR planning
-
Incident-driven continuity decisions
-
Backup validation
-
Crisis communication
-
Recovery testing
Domain 29: Legal, Ethics & Cyber Law
-
Legal considerations in investigations
-
Evidence handling requirements
-
Privacy and data protection
-
Ethical decision-making
-
Regulatory incident response
Domain 30: Emerging Threats & Future Defense
-
Zero-day threats
-
AI-driven attacks
-
Supply chain compromise
-
Evolving defensive technologies
-
Preparing for future threat landscapes
Exam Alignment
-
Total Domains: 30
-
Exam Duration: 6 Hours
-
Total Questions: 600
-
Format: Scenario-Based MCQs
-
Difficulty: Intermediate to Advanced
-
- Certification
- Any
- 1 Section
- 0 Lessons
- 6 Hours
- Certified Security Defense Engineer (CSDE)1
Enroll This To Start Learning From Today.
Certified Security Defense Engineer (CSDE) is a comprehensive, scenario-based cybersecurity certification designed for blue team and defensive security professionals. The 6-hour exam evaluates real-world skills in threat detection, incident response, SOC operations, and enterprise defense using 600 in-depth MCQs. CSDE is vendor-neutral, industry-aligned, and focused on practical decision-making rather than memorization, making it an ideal credential for professionals seeking to validate advanced cybersecurity defense expertise.
You might be interested in
-
All levels
-
56 Students
-
0 Lessons
-
All levels
-
56 Students
-
0 Lessons
-
All levels
-
51 Students
-
0 Lessons
-
All levels
-
51 Students
-
0 Lessons
-
All levels
-
60 Students
-
0 Lessons
-
All levels
-
60 Students
-
0 Lessons
-
All levels
-
56 Students
-
0 Lessons
-
All levels
-
56 Students
-
0 Lessons
Sign up to receive our latest updates
Get in touch
Call us directly?
Visit Us
Need some help?
Partners List
- © 2026 SecByte.org rights reserved.